When you create an AWS account with an user name, that user is called Root user, this user is the super user and has access to all resources on AWS, so it is very important to keep this account safe and secure and not share with any other users for accessing AWS.
Best practices to secure AWS accounts How to create User Groups through AWS IAM console How to create User Accounts through AWS IAM console What are IAM policies What are IAM roles What is Access Analyzer and how to create one using AWS IAM Console
It is important to keep your AWS accounts safe and secure as these accounts will have access to AWS resources. Below are some best practices to keep the accounts safe and secure.
- Use temporary credentials for human user accounts such as administrators, developers, support team etc when accessing AWS accounts. You can use an identity provider for your users to provide federated access to AWS accounts by assuming roles, which provide temporary credentials.
- For the centralized access, AWS recommend to use
IAM Identity Center to manage access across accounts. - Use IAM roles to grant access to resources.
- Enable MFA (Multi Factor Authentication) for root users, so that each time when you try to login it sends a token to your mobile device and you need to confirm that token.
- Rotate keys more frequently where an AWS account uses long term credentials.
- Apply least privilege permissions for accounts that perform tasks on AWS resources.
- Use AWS managed policies as a template, make a copy of that and add or remove privileges that are not needed for the role.
User Groups are a way of organizing different users who needs different level of access permissions based on job duties or role in the company. You can create different user groups to meet these needs like admin group, developers group, devops group or support group etc.
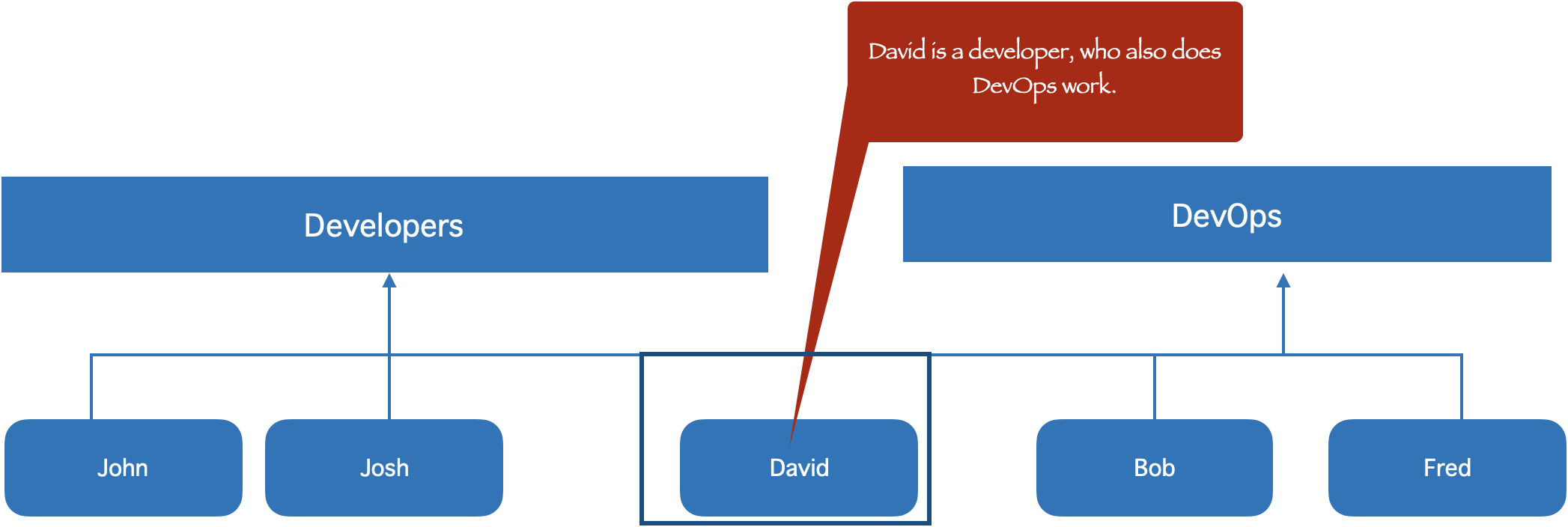
For example, say if there are two different teams in your oraganization Developers and DevOps, then you would typically create two user groups, Developers team who requires access to all development and debugging tools etc. and DevOps group may need different set of access permissions.
An user can belong to more than one group, in the below example David belongs to developers group, but also does DevOps work, in this case you can add David to both groups.
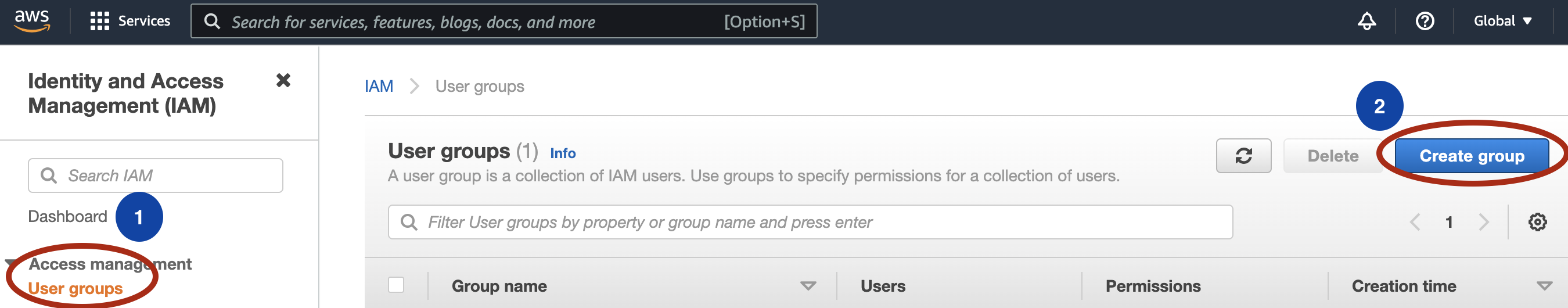
- To create an User group from AWS Identity and Access Management console, click on User groups and then Create group.
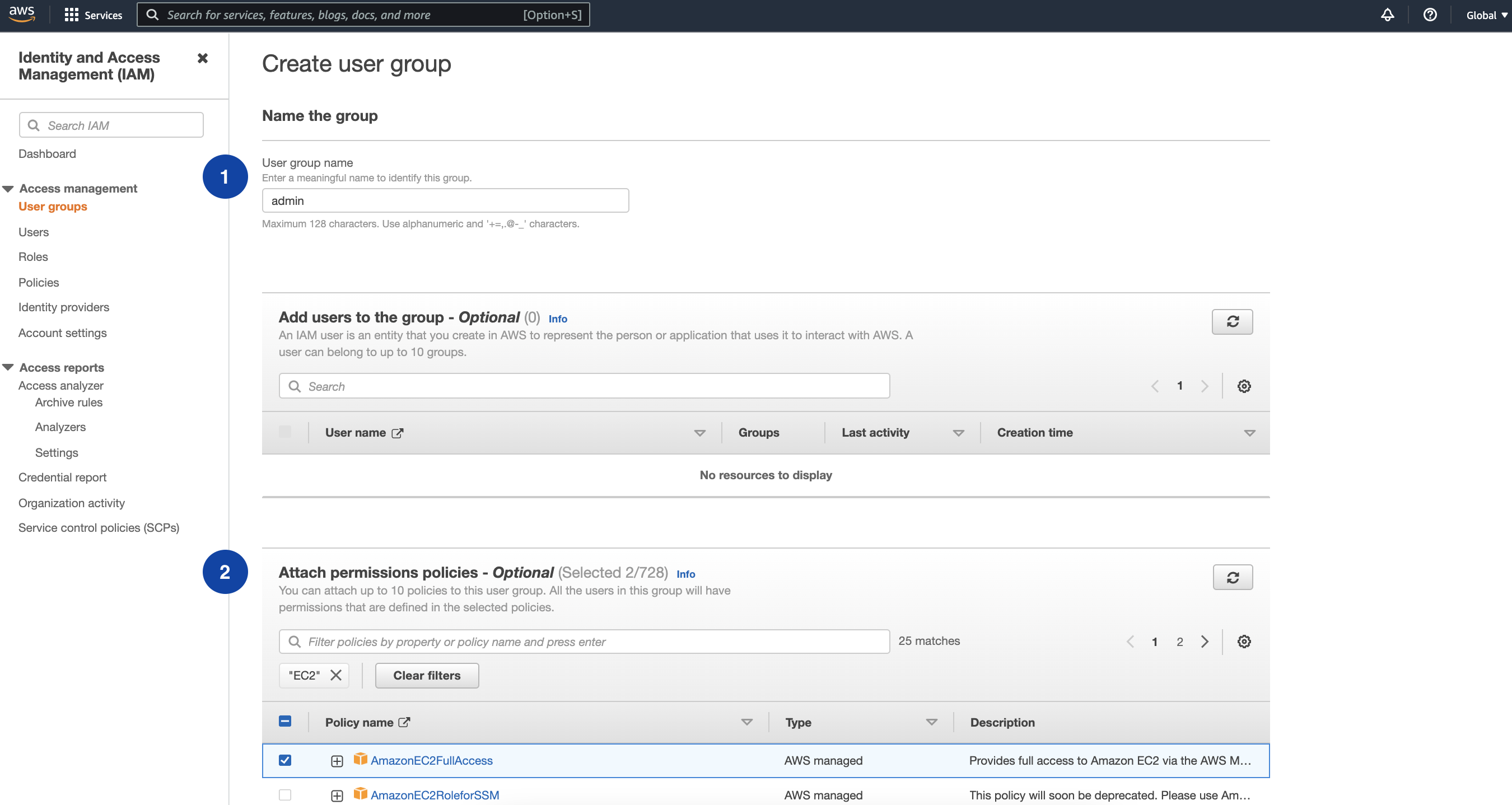
- In the next step, provide a name for User group name and attach permissions policies. Attaching policies at this step is optional as you can always create user group as a place holder and then attach policies at a later time.
You can also
In order to access AWS resources for different use cases like development, deployment, support or accessing an API/SDK, it is always a best practice to create user accounts for each of the users who needs access.
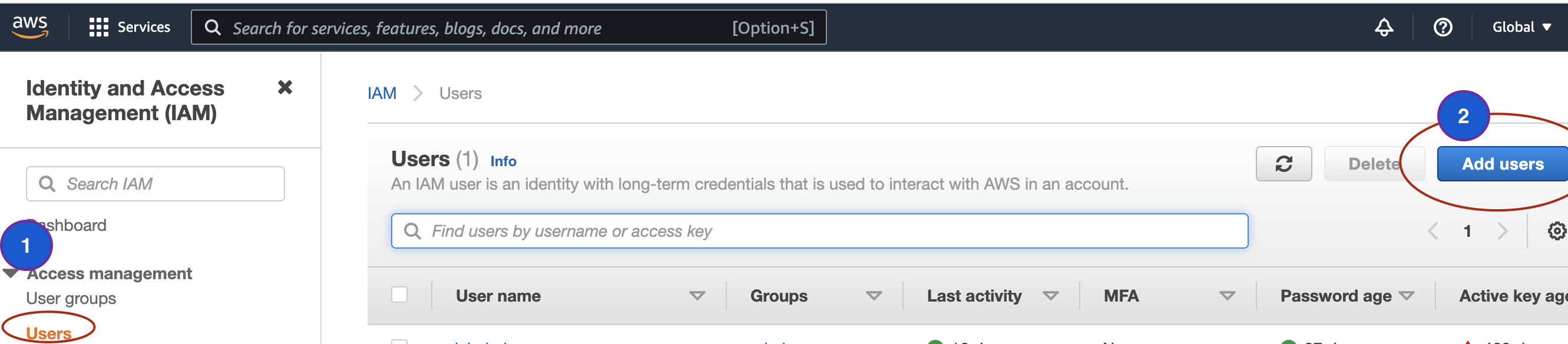
- To create user from AWS Identity and Access Management console, click on Users and then Add Users.
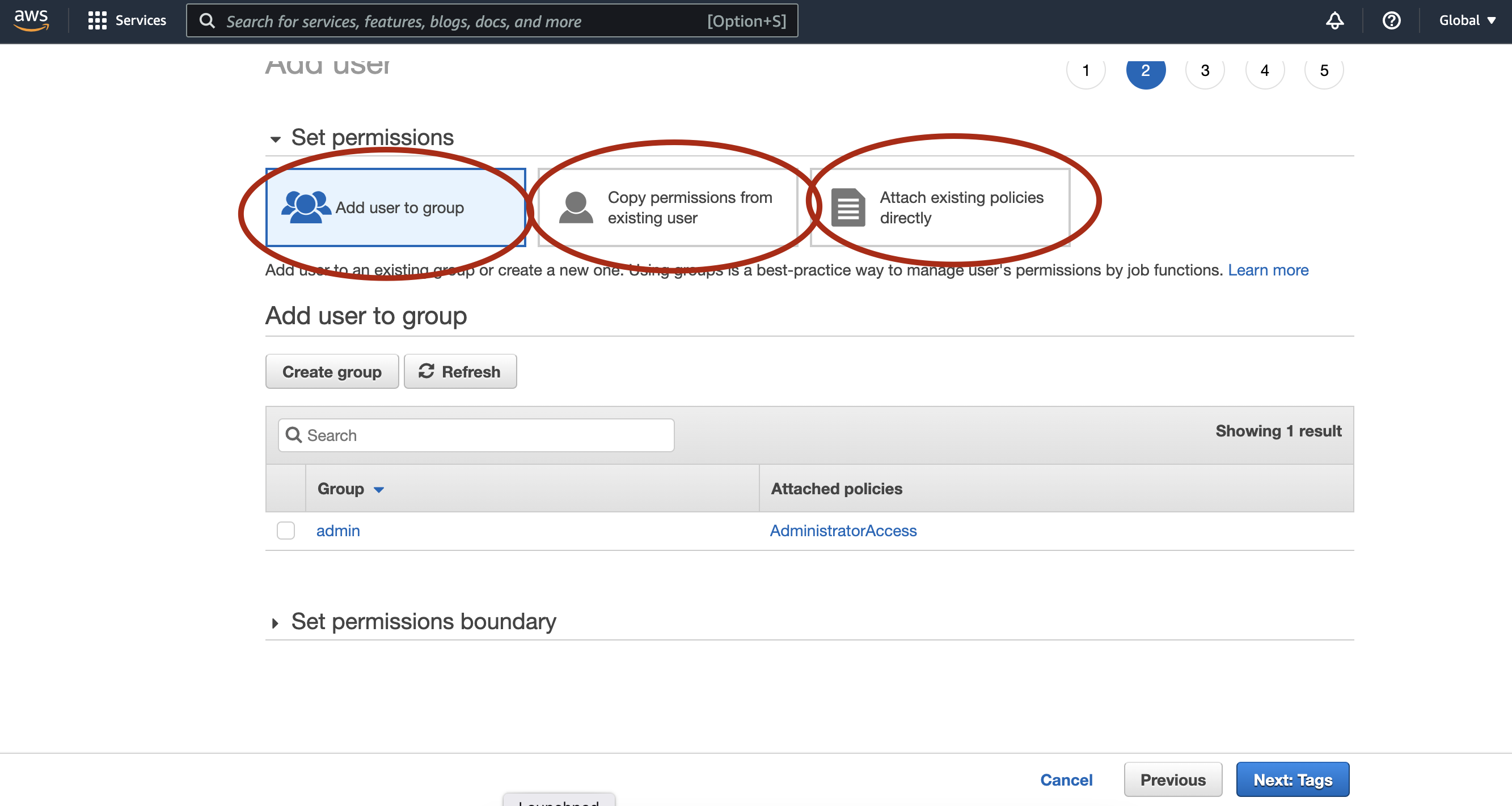
- In the next screen, set permissions to the user, there are three different ways to do that. Add the user to any user groups if you have already created, by doing so this user will inherit access permissions from the user group, or you can copy permission from another existing user, or you can attach access policies directly to the use at this step.
- In the next step, you can create tags as you wish and complete user creation process. (Tags can help you manage, identify, organize, search for, and filter resources).
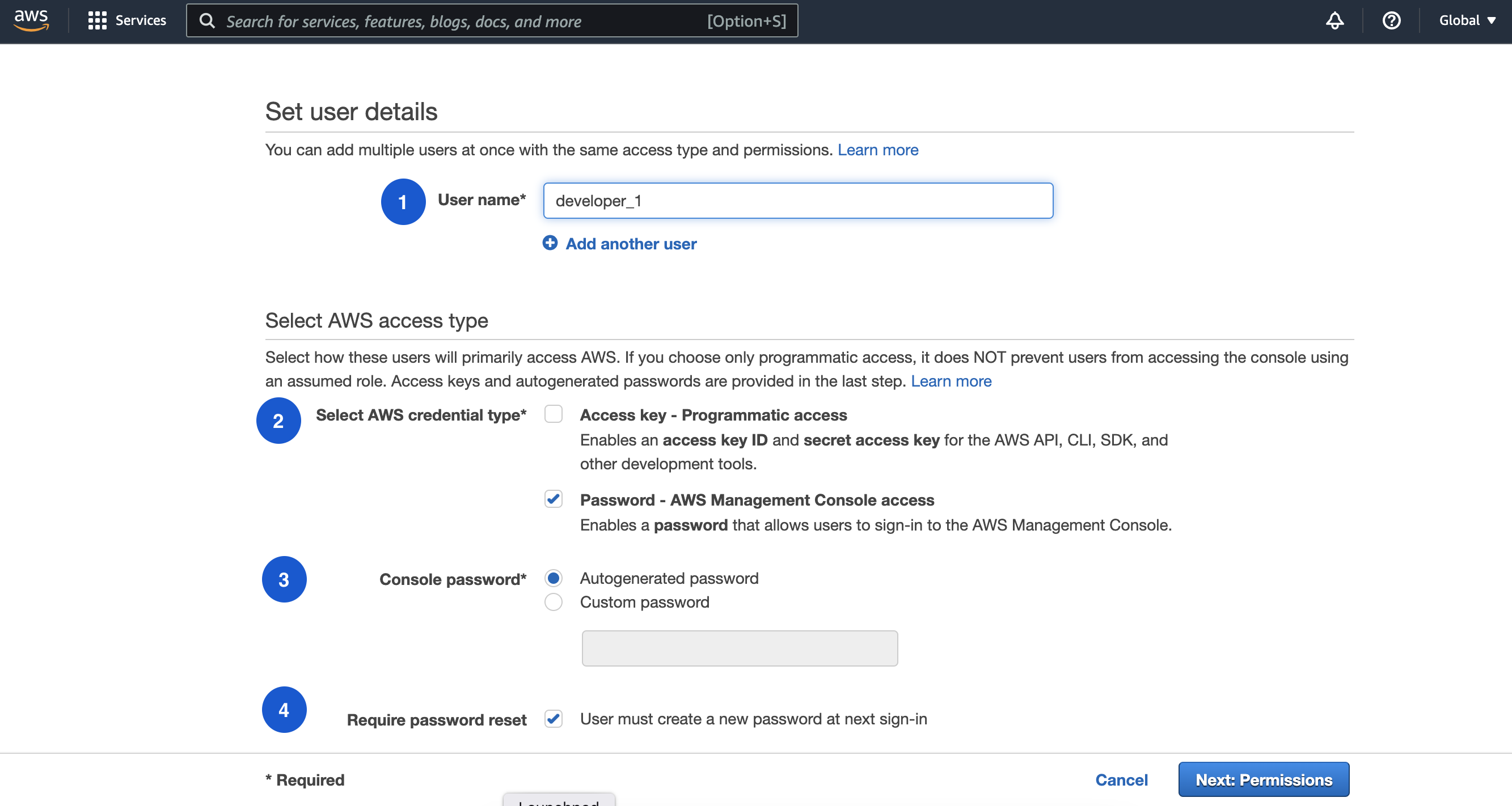
Enter user name in the User name field and select AWS credential type, if the user account is intended for accessing AWS console and access resources, then choose Password as credential type and if the user account is intended for API or SDK access only, then choose Access Key as credential type or if the user account can have both accesses then select both options.
Then select Require password reset option if you want to force the user to change the password upon next login.
You can also
An IAM Policy is a fine granular level definition where you define access permissions to an AWS resource, think of it as a placeholder where you actually define the access permissions and assign these policies to individual users, users group, systems or other AWS services. IAM Policy definition is a JSON document that describes the access permissions to AWS resources, within one IAM policy JSON document you can define access permissions to more than one AWS resource.
For example, you can define who can access an
There are several AWS managed IAM Policies that are already built by AWS that we can simply pick and choose based on the need.
These AWS managed policies comes handy when you are going to start from scratch, below is an example of AWS managed policy, AmazonEC2FullAccess it has all the access privileges pre-defined for EC2 resource full access.

You can also create your own Policies and assign access permissions, below steps outlines how to create a new IAM Policy.
Creating your own new policy using AWS Console
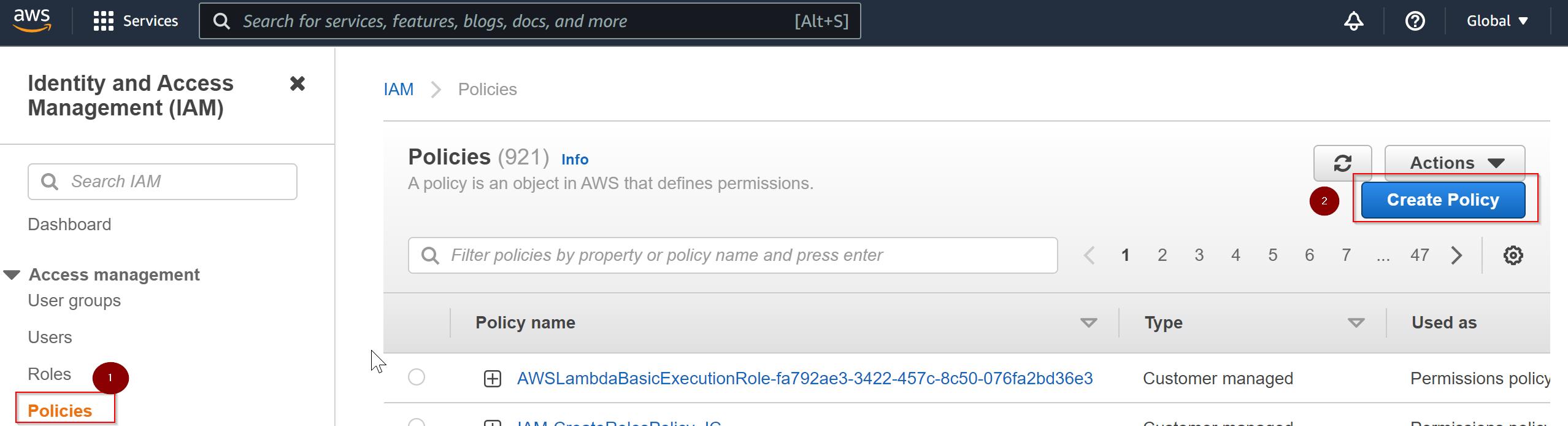
- To create a new IAM policy from AWS console, navigate to Policies and click on Create Policy.
- In the next screen, use Visual Editor to pick and choose the service, action and resources, you can also add multiple services in one go using the option Add additional permissions. Visual Editor comes handy to define access permissions using GUI and behind the scene it generates the JSON equivalent.
- In the next screen, you can add tags (optional) as you wish and complete.
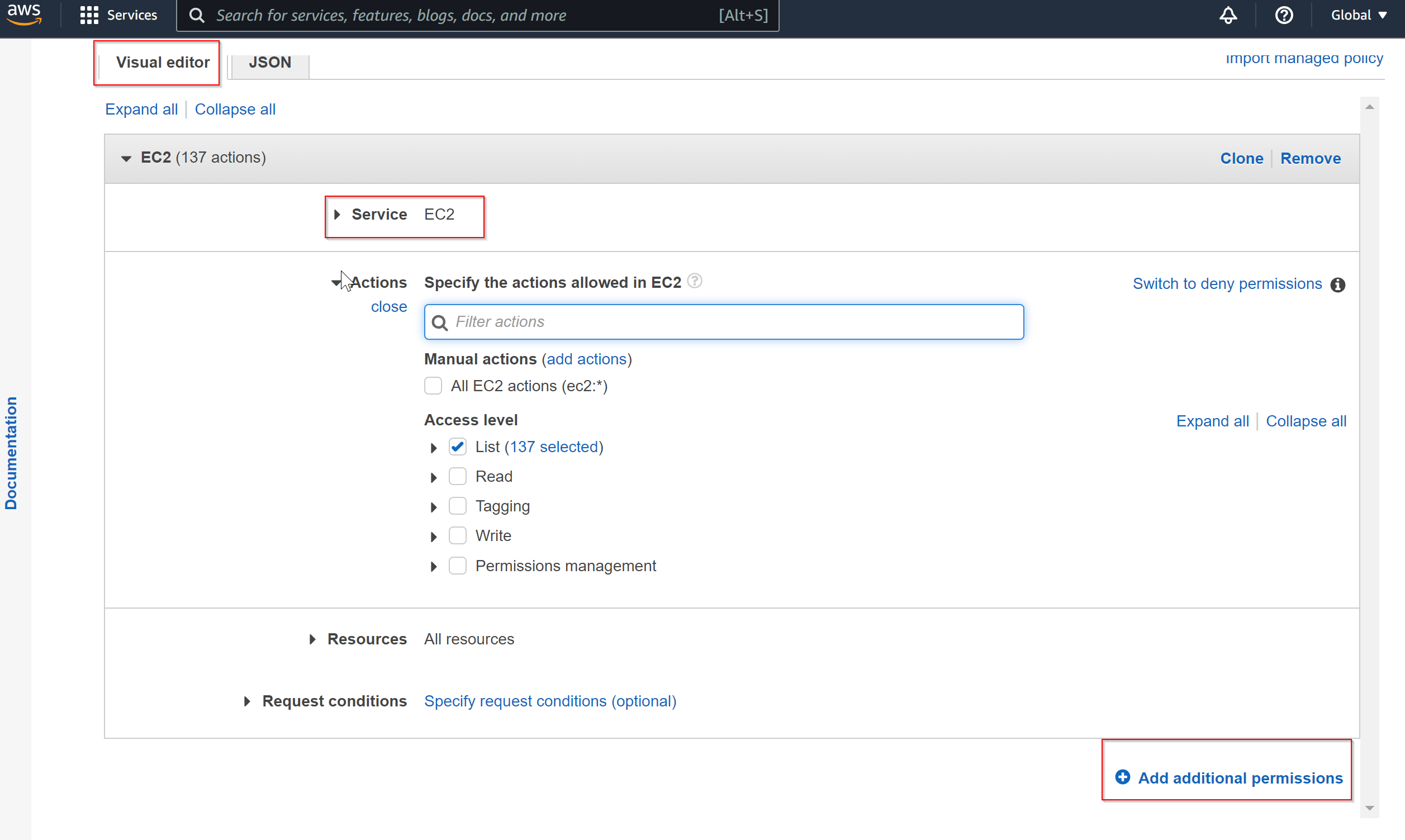
Cloning an AWS managed policy
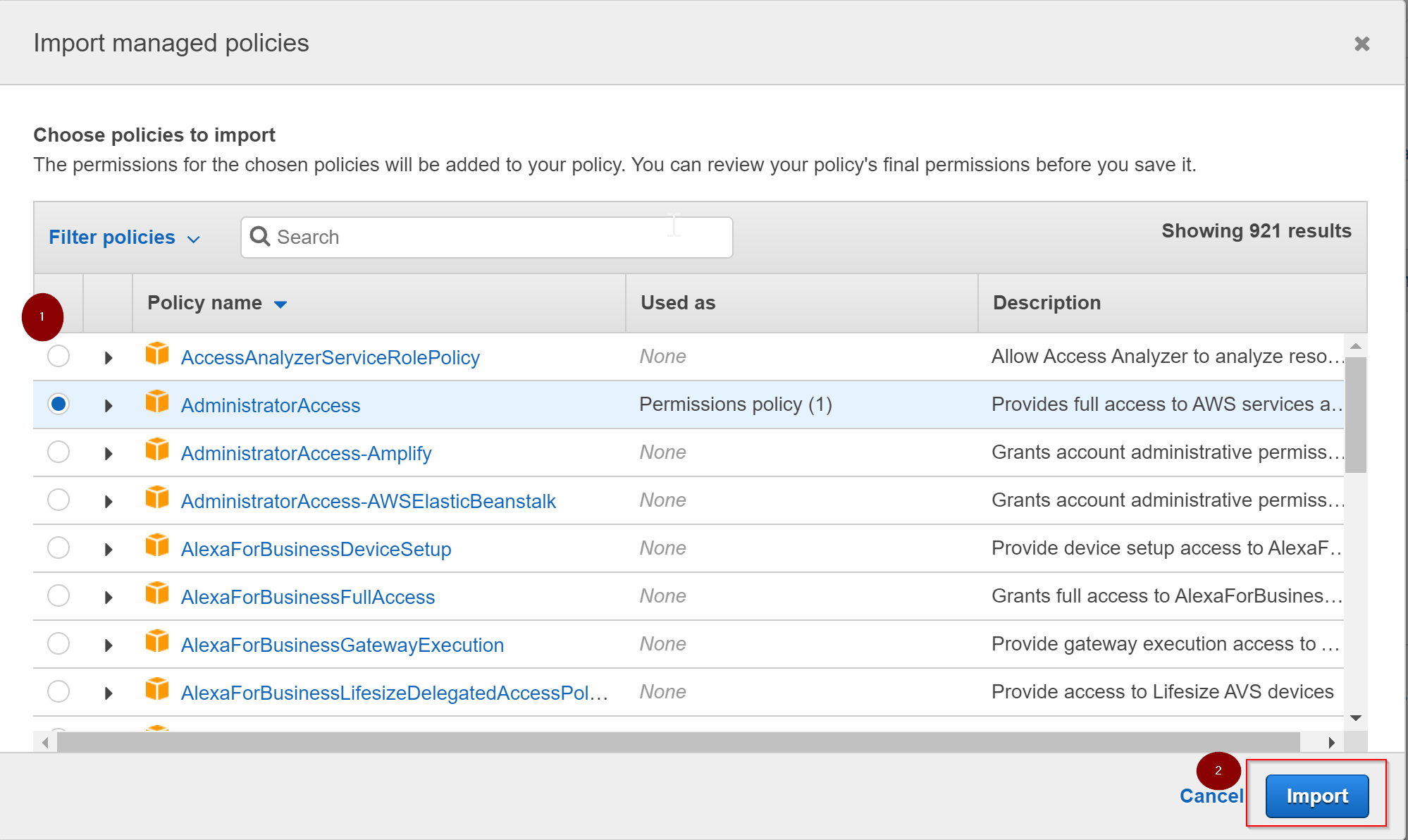
- If you want to clone an AWS managed policy and make your own changes top of that or use it as is, you can select the option 'Import managed policy'
- If you want to create a new IAM policy using a JSON, the syntax looks like below, you can define multiple access permissions under the main Statement element and you can even add more advanced attributes such as Condition attribute to add conditions to a resource access and many other elements.
For complete reference of the JSON elements, please refer to this link
- In the above JSON, Effect element tells whether the permission is Allow or Deny.
Action element tells what the Service name and action name, you can specify it using a wild card or specific action name, for example ec2:* meaning that all actions under EC2 service and ec2:StartInstances meaning that StartInstances action under EC2 service.
Resource element specifies the object or objects that the statement covers.
You can also
IAM role is an identity that you can create in your account and provide access permissions to AWS Services, other AWS accounts and third party applications such as OpenID providers or your own organization SAML provider.
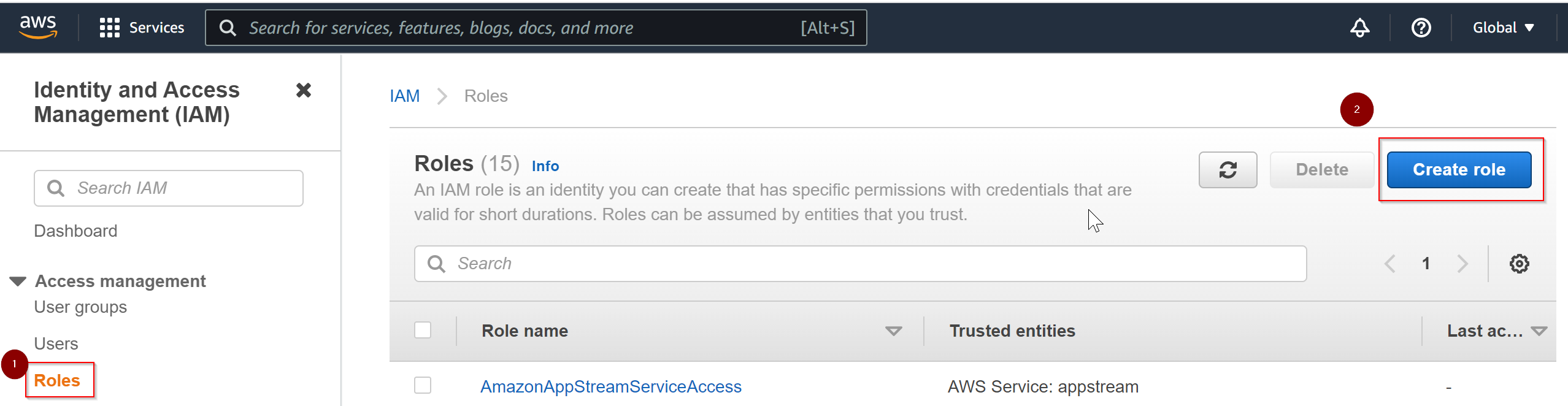
- To create a new IAM role, navigate to Roles section from AWS IAM console, and click on Create role button.
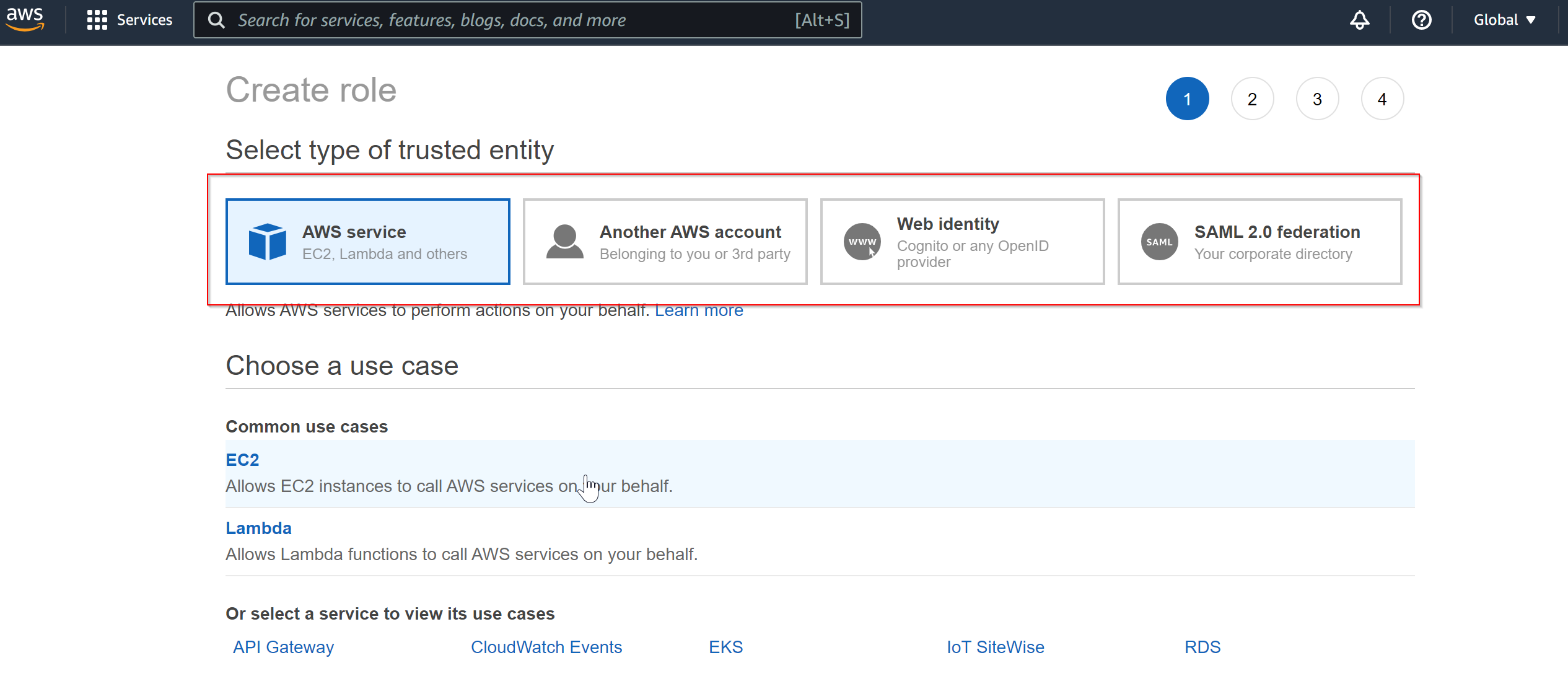
- In the next screen you will be prompted with 'type of trusted entity', here you need to select the type of entity where you will be assigning this role to.
- Select 'AWS Service' if you are going to assign this role to an AWS service as EC2, S3 or Lambda function etc.
- Select 'Another AWS account' if you are going to assign this role to another user account.
- Select 'Web Identity' if you are going to assign this role to a third party OpenID provider such as Facebook or Google.
- Select 'SAML 2.0 federation' if you are going to assign this role to a SAML provider.
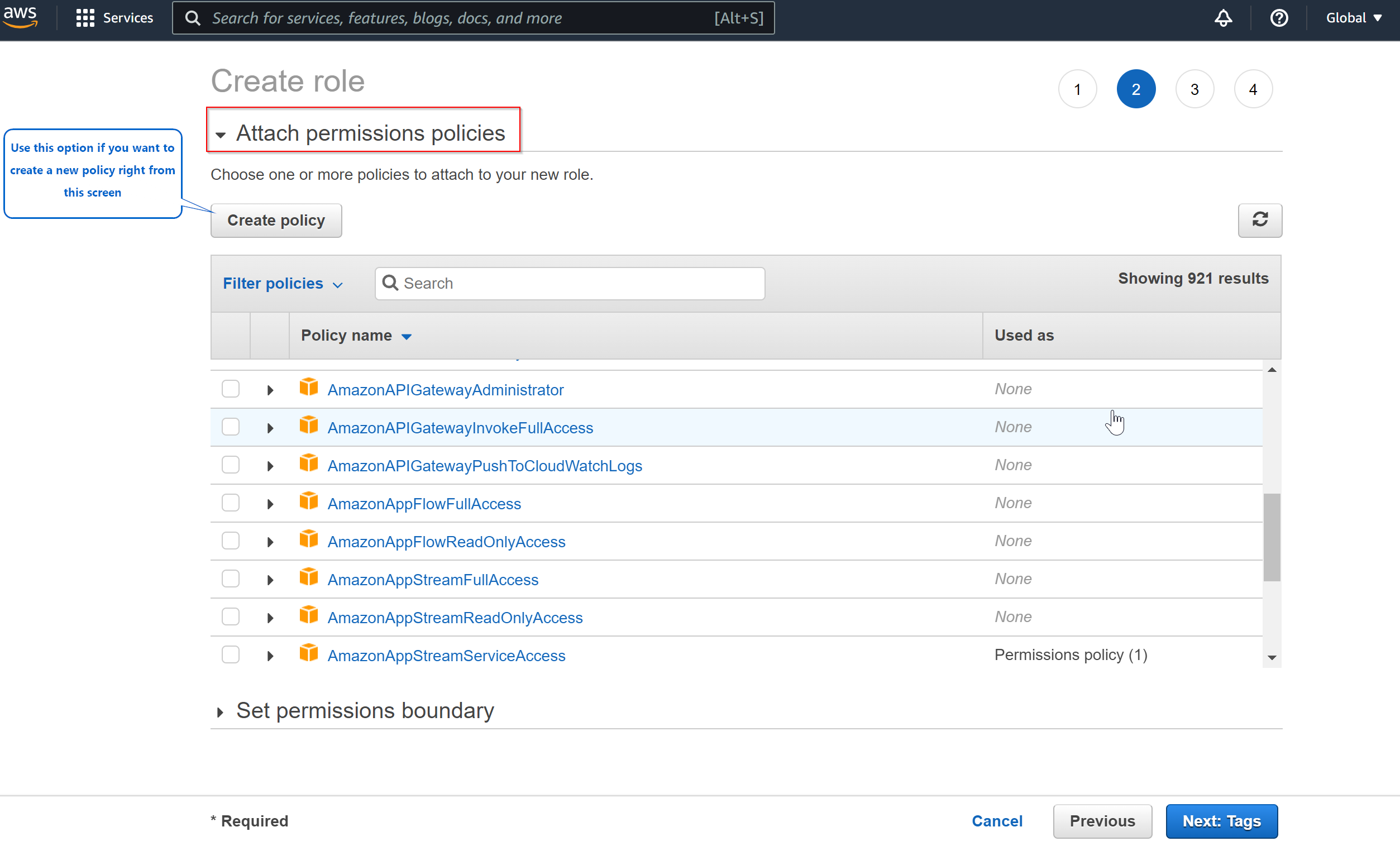
- In the next step, you will be prompted to choose 'Attach permissions policies', here you can choose the policiies either AWS Managed policies or your own policies or you can also create a new policy from this screen.
- In this step, you can also set permissions boundary for this role, meaning that a super set of permission that it cannot exceed.
- In the next step, add tags as you wish and complete the role creation.
You can also Create IAM Role using AWS CLI and Create IAM Role using AWS SDK.
Access Analyzer is a tool available under IAM which helps in analyzing access permissions to AWS resource within an AWS Region.
While IAM service is a Global service, but Access Analyzer is bound a specific AWS region, so if you are planning to use this tool, then you need to create one per AWS Region.
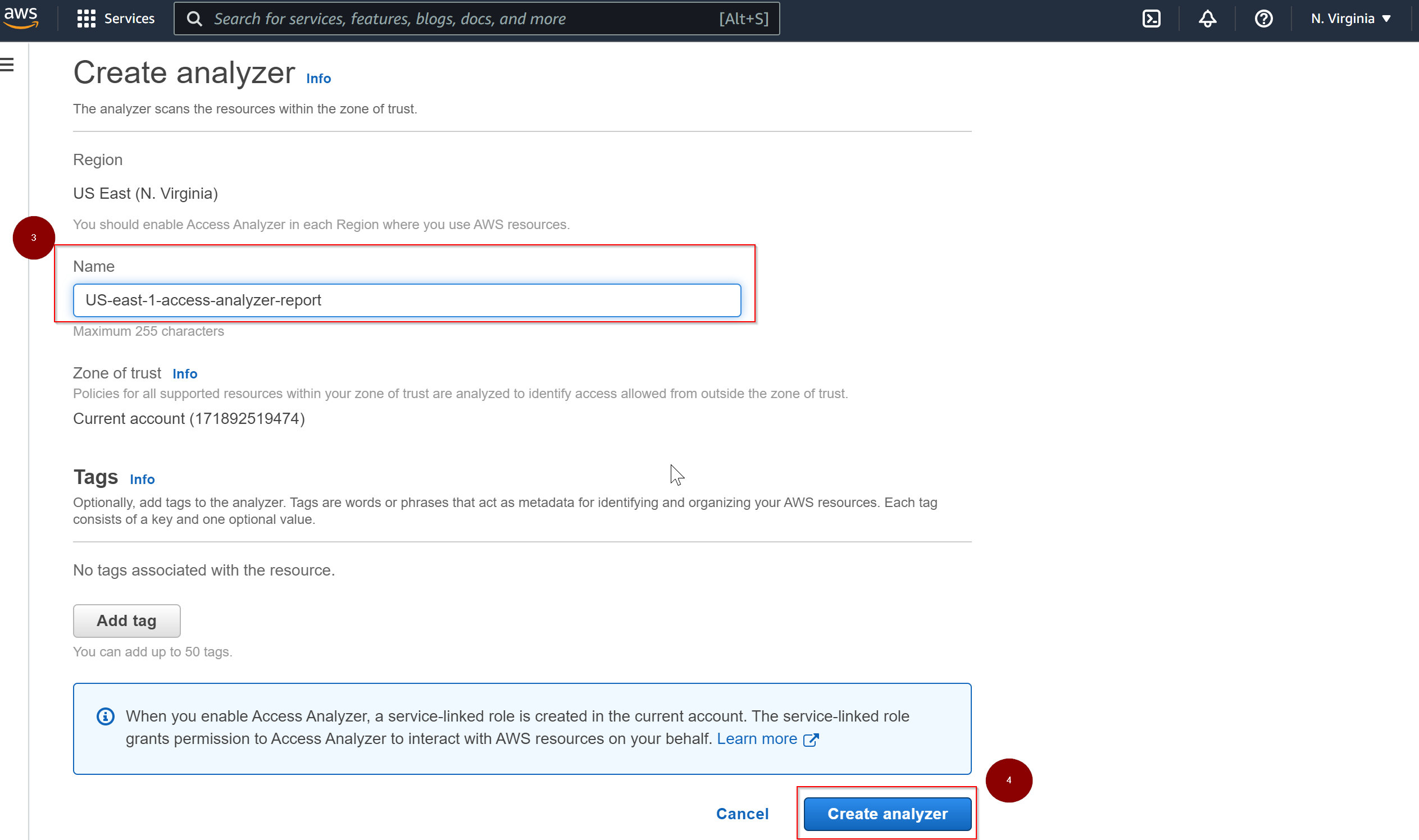
In order to create Access Analyzer report, go to IAM console and choose the option Access Analyzer under Access reports and click on 'Create analyzer'
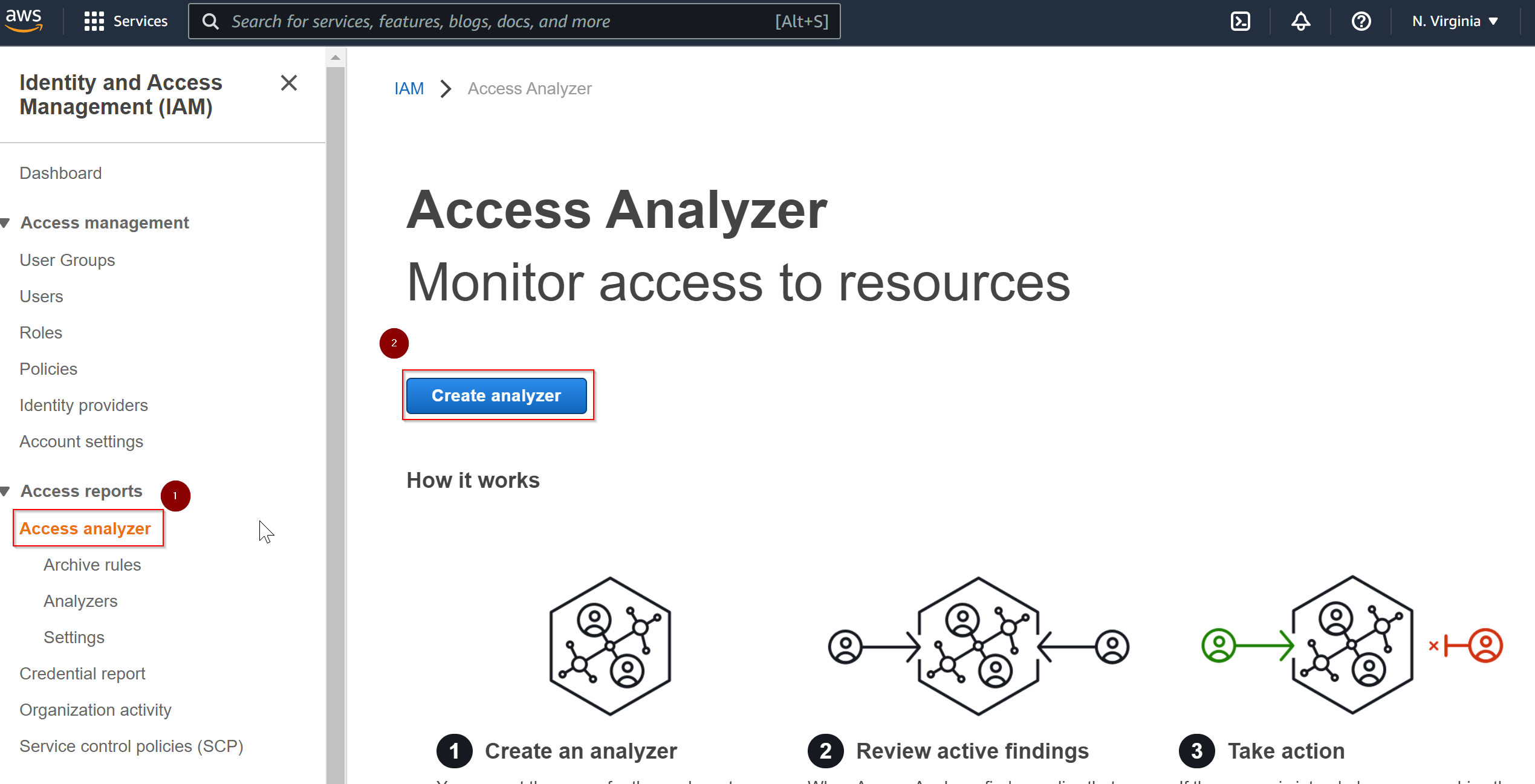
In the next step, give a name to the access analyzer report and create analyzer.